Jill Scharr
Jill Scharr is a creative writer and narrative designer in the videogame industry. She's currently Project Lead Writer at the games studio Harebrained Schemes, and has also worked at Bungie. Prior to that she worked as a Staff Writer for Tom's Guide, covering video games, online security, 3D printing and tech innovation among many subjects.
Latest articles by Jill Scharr

WhatsApp Flaw Makes Your 'Private' Messages Easy to Read
By Jill Scharr published
Popular and messaging app WhatsApp backs up messages on Android in an insecure way, according to one security researcher.

Blackphone vs. FreedomPop's Privacy Phone: Security Showdown
By Jill Scharr published
Want a private phone? We compare FreedomPop's "Privacy Phone" and the Blackphone from Silent Circle and Geeksphone.

New Tool Lets Anyone Turns Android Apps Into Malware
By Jill Scharr published
Crime goes commercial: Dendroid is a $300 toolkit selling on the black market that transforms apps into malware.
Facebook Scam Promising Naked Videos Infects Millions
By Jill Scharr published
Malware promises naked videos of your Facebook friends, but instead infects your computer, then moves on to infect others.

Critical Linux Flaw Threatens More Systems Than You Think
By Jill Scharr published
A newly discovered bug in open-source encryption software leaves Web traffic vulnerable to attack and affects more systems than you think.

New 'Batman: Arkham Knight' Video Game Leaked - UPDATED
By Jill Scharr published
The Dark Knight returns! Leaked 'Batman: Arkham Knight' video game is a sequel to 'Arkham City' and will let players drive the Batmobile.

Wi-Fi-Hopping Malware Behaves Like Actual Virus
By Jill Scharr published
A new piece of malware spreads rapidly over Wi-Fi through densely populated areas, much like a disease spreads through crowded urban areas.

How to Upgrade Snow Leopard to OS X Mavericks
By Jill Scharr published
Apple has probably ended support for Mac OS X Snow Leopard 10.6. Here's how to make the free upgrade to Mavericks.

New Android Malware Uses Tor Privacy Network
By Jill Scharr published
A new type of malware intercepts your text messages and, for the first time on Android, uses the Tor privacy network to cover its tracks.
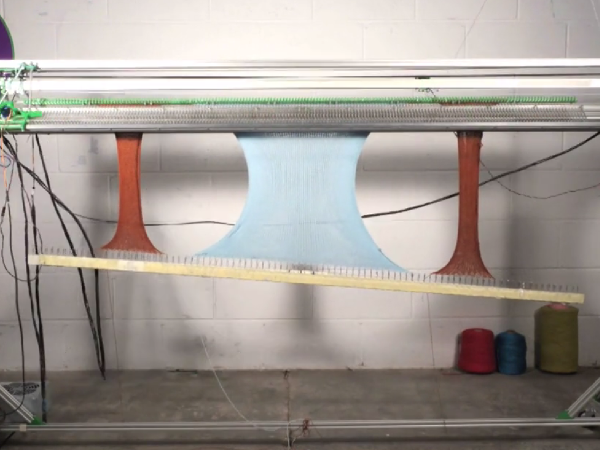
Beyond 3D Printing: OpenKnit is a 3D Knitting Machine
By Jill Scharr published
The OpenKnit is a 3D-printer-like machine that can 'print' knitted clothing from a .STL file.

Why Not to Believe 'Talking Angela' or Other Facebook Hoaxes
By Jill Scharr published
Don't believe hysterical Facebook posts about 'Talking Angela,' the harmless app rumored to be a front for pedophiles.

How Secure Is WhatsApp?
By Jill Scharr published
WhatsApp is on the up and up, recently bought by Facebook for a whopping $19 billion. But the app has had more than its share of security and privacy issues in the past few years too.

How to Encrypt Your Files and Folders
By Jill Scharr published
When it comes to encrypting your files, you have a lot of options. Here are a few good ways to encrypt your files and folders.

How to Encrypt Files on iOS
By Jill Scharr published
On iOS, encrypting your device is as easy as setting a passcode. Here's how to do it.

How to Update Your Linksys Router
By Jill Scharr published
Protect against TheMoon worm by upgrading your Linksys router to the latest firmware and following these instructions.

How to Encrypt Files on Mac OS X
By Jill Scharr published
Mac OS X computers have some built-in encryption features. Here's a step-by-step tutorial on how to encrypt files and folders.

Soulmate or Cybercriminal? How to Avoid Online Dating Scammers
By Jill Scharr published
Love is in the air—but it's not everywhere. If your online sweetheart asks you for money or is too hot to be true, it could be a scam.

Aviator: Hands-On With the Most Secure Web Browser
By Jill Scharr published
The new Aviator browser aims to fly high above the competition with its enhanced privacy and security features.

Blaming Violence on Video Games Does More Harm Than Good, Researcher Says
By Jill Scharr published
Don't believe the hype: The latest study linking video games and antisocial behavior is just as flawed as the rest of them.

Top 50 Steam Machine Games 2014
By Jill Scharr published
SteamOS is based on the Linux operating system, so only Steam's Linux-compatible games, which currently number 502, can be played on it.

Over a Third of iOS, Android Apps Snoop on Your Location
By Jill Scharr published
A huge number of iOS and Android apps can track and record your location, according to a Bitdefender report.

ICE Unlock Hands-on: App Adds Fingerprint Security to Android
By Jill Scharr published
The new ICE Unlock Android app lets Android phone owners unlock their devices via the rear-facing camera, but how well does it work?

'Spoiled Onions' in the Tor Network, Researchers Find
By Jill Scharr published
Swedish researchers found 22 corrupted exit nodes that were tampering with encrypted data leaving the supposedly private Tor network.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Here at Tom’s Guide our expert editors are committed to bringing you the best news, reviews and guides to help you stay informed and ahead of the curve!


