Mac Anti-Ransomware Tool Released, but Needs More Work
A new tool promises to immunize Macs against encrypting ransomware, but someone's already found a way around its defenses.
Worried that ransomware might infect your Mac? Then you might want to try famed Mac hacker Patrick Wardle's new RansomWhere tool, which will try to detect and stop encrypting ransomware dead in its tracks.

"Unless you've been living under an infosec rock, you're likely aware that ransomware is somewhat of a problem — to put it mildly," Wardle, a researcher with Silicon Valley security firm Synack, wrote in a blog post. "There are already claims that '2016 is shaping up as the year of ransomware' and that 'this is basically becoming a national cyber emergency.'"
However, Wardle's own tool may have its limitations. Pedro Vilaca, a Portuguese Mac hacker, posted a video showing a quick and easy way around RansomWhere this morning (April 20), only a few hours after Wardle had unveiled his utility.
MORE: What Is Ransomware and How Can I Protect Myself?
Several strains of encrypting ransomware have been targeting Windows PCs and servers, and more recently Linux servers, all across North America. Hospitals, schools and municipal government agencies have had to pay thousands of dollars to free their files, and the average PC user often must pay a few hundred dollars to regain access to his or her documents.
Macs aren't immune to this threat. In March, we saw KeRanger, the first known piece of encrypting ransomware targeting Macs "in the wild." It didn't work entirely properly, but the next strain of Mac ransomware will be more effective.
So Wardle took a hint from security-software makers Malwarebytes and Bitdefender, which have released their own ransomware-detection tools for Windows, and created his own, free anti-ransomware tool for OS X.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
RansomWhere? (the question mark is part of the name, but we'll not use it from now on) starts upon boot and runs in the background to keep an eye out for non-Apple-approved processes that start rapidly encrypting files in the user's Home directory.
"If we can monitor file I/O [input/output] events and detect the rapid creation of encrypted files by untrusted processes, then ransomware may be generically detected," Wardle figured.
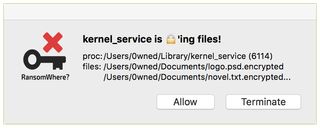
If RansomWhere spots such a process, it will suspend the process and pop up an alert window to notify the user. The window will show the file path of the suspect process, and the file paths of those that have already been encrypted.
If the user recognizes the encryption process as legitimate, he or she can click Allow to let the process resume. If not, he or she can click Terminate to end the process.
Vilaca's video, however, showed that he had created a proof-of-concept piece of ransomware called RansomNowhere that encrypted files in Vilaca's own Home folder.
"RansomWhere is a cool attempt but it's very much flawed," Vilaca tweeted. "Look at it as a PoC [proof of concept] and that's it."
Wardle hadn't responded to Vilaca's demonstration by the time of this piece's publication, but he did warn in his blog posts that RansomWhere was just the beginning.
"Both this research and tool are version 1.0, meaning likely room for improvement," Wardle wrote.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.
