Stealthy Botnet Bug Infects Macs, PCs, Linux Machines
A sophisticated Java-based Trojan herds Macs, PCs and Linux machines alike into cyberattack-launching botnets.
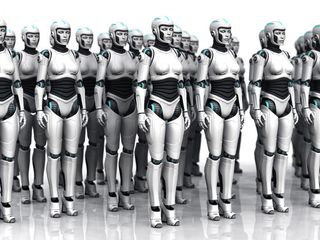
The more complex software gets, the more complex malware becomes in return, as a new Trojan that infects Windows PCs, Macs and Linux boxes alike demonstrates.
The Trojan, dubbed "HEUR:Backdoor.Java.Agent.a" by researchers at Kaspersky Lab in Moscow, is written entirely in Java, the independent software platform that can be installed on almost any computer.
Once infected, likely through a malware-hosting website, a computer compromised by this Trojan is drafted into a botnet, an array of machines secretly controlled by remote administrators, and used to launch distributed denial-of-service attacks against other websites, knocking them offline temporarily.
MORE: 12 More Things You Didn't Know Could Be Hacked
The only silver lining in this dark cloud of online crime is that the Java vulnerability the Trojan exploits was patched back in June 2013. If you're diligent about keeping Java updated — or, better yet, don't have it on your computer at all — you're safe.
Unfortunately, Java must be updated manually, which means millions of people haven't patched their installations and are sitting ducks for this and other kinds of Java malware.
Every malware trick in the book
HEUR:Backdoor.Java.Agent.a has a grab bag of tricks to make sure it's hard to detect or remove.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Upon infecting a Java installation, the bug senses whether it's on a Mac, PC or Linux box, and adjusts its routine accordingly. On a PC, the Trojan modifies the Registry to make sure the botnet software launches with Windows. On Mac OS X and Linux, it modifies the launchd and init.d files, respectively, to the same end.
The bug incorporates a code obfuscator, rearranging bits and bytes to make it difficult for anti-virus researchers to take apart and difficult for anti-virus software to spot. Parts of the code are even encrypted.
Each infected machine, or "bot," gets its own ID for efficient botnet management. The bots are controlled via the durable Internet Relay Chat (IRC) protocol, a 25-year-old instant-messaging protocol, and each installation includes an open-source Java-based IRC bot framework for greater functionality.
Over IRC, the botmaster assigns IP addresses of websites to be attacked, port numbers through which to flood targeted servers and durations of planned attacks. During an attack, each bot will randomly select a user-agent string with which to impersonate certain browsers and platforms.
How to protect yourself from Java malware
The first line of defense you can take against HEUR:Backdoor.Java.Agent.a is to update all installations of Java on every Mac, Windows or Linux computer you own.
That includes the stand-alone Java Runtime Engine (JRE), which is used to run games and facilitate communication among some Adobe applications, as well as Java browser plugins, most commonly used for Web conferencing and remote-desktop software.
However, if you don't currently have Java installed, then don't install it. The platform is prone to serious malware exploitation, and malicious coders are finding new vulnerabilities in Java all the time.
Even machines with rock-solid defenses fall prey to Java malware. In January 2013, Apple, Facebook and Microsoft had their corporate systems penetrated by a Java bug that infected Macs belonging to staff software developers.
If you must use the JRE, install it on its own, and don't accept any browser plug-ins. (Web browsers are the most common route of Java infection.)
If you must use a Java-enabled Web browser for a specific purpose, then install a Java plugin on one designated browser, and use that browser only for that specific purpose — no emailing, no social media, no random surfing around.
Otherwise, you'll just be asking for trouble.
Follow Paul Wagenseil at @snd_wagenseil. Follow Tom's Guide at @tomsguide, on Facebook and on Google+.
Paul Wagenseil is a senior editor at Tom's Guide focused on security and privacy. He has also been a dishwasher, fry cook, long-haul driver, code monkey and video editor. He's been rooting around in the information-security space for more than 15 years at FoxNews.com, SecurityNewsDaily, TechNewsDaily and Tom's Guide, has presented talks at the ShmooCon, DerbyCon and BSides Las Vegas hacker conferences, shown up in random TV news spots and even moderated a panel discussion at the CEDIA home-technology conference. You can follow his rants on Twitter at @snd_wagenseil.











-
tuxitca "On Mac OS X and Linux, it modifies the launchd and init.d files"Yeah, good luck with that. How many people do you think run their browser as root anyway?Reply -
iamtracyanne quote:: "On Mac OS X and Linux, it modifies the launchd and init.d files"Yeah, good luck with that. How many people do you think run their browser as root anyway? ::quoteIn addition most Linux installs these days run a Free open Source implementation of Java, such as IcedTea. Not Oracle's Java, which has to be downloaded from Oracle, unlike IcedTea, which comes pre installed, and is updated automatically via the Package management system.Reply -
NickyHelmkamp Paul- fantastic article! We just wanted to let you know that we included it in our Monthly Resource Roundup http://www.interworx.com/community/monthly-round-januarys-best-administration-hosting-security-enterprise-content/Reply





