Avoid This Fake, Data-Stealing Chrome Update
A fake update to Chrome for Android is tricking users into exposing their call and text logs and banking information.
Chrome for Android receives updates through the Google Play Store, but users unaware of that may be more likely to fall prey to newly discovered malware that steals calling, texting and banking information. Making matters worse, the thieving Update_chrome.apk file evades antivirus software and cannot be removed without wiping your device.

The malware was discovered in the wild yesterday (April 28) by California-based security firm Zscaler. The firm has not reported a point of origin for the attacks, but it observed that the files are being downloaded from web pages whose addresses look like they could host Google or Android updates, such as “http[:]//android-update15[.]pw/”.
MORE: Mobile Security Guide: Everything You Need to Know
After downloading the APK file, users would need to disable one of Android’s default security settings which prevents the installation of programs from unknown sources. Once that’s done and the target gives Update_chrome.apk administrative access, the malware registers the phone with its remote server, and monitors all SMS messages and calls, which it sends to remote servers.
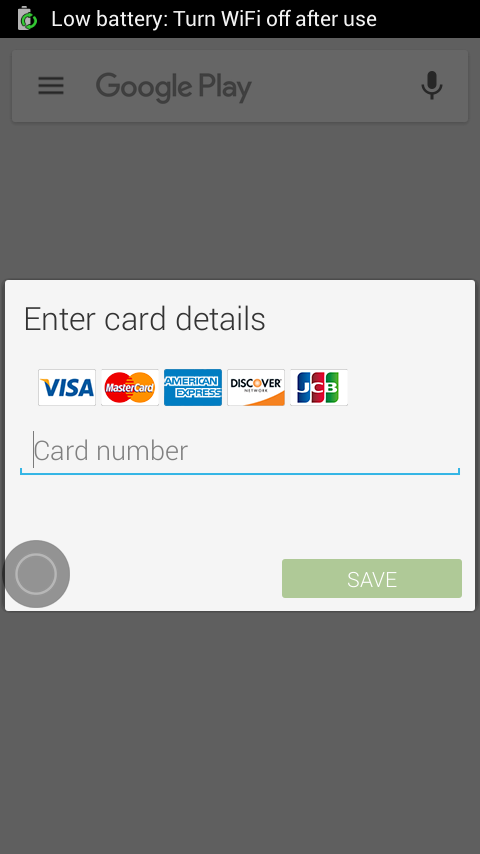
If users open the Play Store on an infected device, the malware presents a phony payment information page for entering credit card numbers. After that data is entered, a screenshot is then sent to a phone number in Russia, which doesn't sound like a safe way to store your banking data.
Android anti-virus software often detects malicious files, but Update_chrome.apkincludes “hard coded checks for antivirus applications like Kaspersky, ESET, Avast and Dr. Web.” After the antivirus suites are found, the malware wipes them from the device, so it can operate without restriction.
The addresses that host the file only exist for short amounts of time, which makes it more difficult for anti-virus filters that use URL-based filtering to detect websites that should not be opened.
Sign up to get the BEST of Tom's Guide direct to your inbox.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
According to Zscaler’s Director of Security Research Deepen Desai, Update_chrome.apk is spreading via “compromised or malicious websites using scareware tactics or social engineering.” Desai told ZDNet that the firm has seen Android malware use “scareware tactics where the user will see a popup indicating that their device is infected with a virus and asks them to update to clean up infection."
Unfortunately, once this software is installed onto a device, it can only be removed by doing a complete factory reset. As always, we suggest that you don't change the setting that allows for installation of apps from unknown sources, and to only download and install software from approved first-party stores like Google Play.

Henry is a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom's Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He's also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
